ip address block after limit cross php
If you want to implement IP address blocking after a certain limit is crossed, you can use PHP along with some form of persistent storage to keep track of the number of requests from each IP address. Here’s a simple example using a file to store the request count for each IP:
// Function to get the client’s IP address
function getClientIP() {
$ipaddress = ”;
if (isset($_SERVER[‘HTTP_CLIENT_IP’]))
$ipaddress = $_SERVER[‘HTTP_CLIENT_IP’];
else if(isset($_SERVER[‘HTTP_X_FORWARDED_FOR’]))
$ipaddress = $_SERVER[‘HTTP_X_FORWARDED_FOR’];
else if(isset($_SERVER[‘HTTP_X_FORWARDED’]))
$ipaddress = $_SERVER[‘HTTP_X_FORWARDED’];
else if(isset($_SERVER[‘HTTP_FORWARDED_FOR’]))
$ipaddress = $_SERVER[‘HTTP_FORWARDED_FOR’];
else if(isset($_SERVER[‘HTTP_FORWARDED’]))
$ipaddress = $_SERVER[‘HTTP_FORWARDED’];
else if(isset($_SERVER[‘REMOTE_ADDR’]))
$ipaddress = $_SERVER[‘REMOTE_ADDR’];
return $ipaddress;
}
// File to store request counts
$filename = ‘ip_counts.txt’;
// Get the client’s IP address
$client_ip = getClientIP();
// Load existing IP counts from the file
$ip_counts = file_exists($filename) ? json_decode(file_get_contents($filename), true) : [];
// Set the limit for requests
$request_limit = 10;
// Check if the IP address has exceeded the limit
if (isset($ip_counts[$client_ip]) && $ip_counts[$client_ip] >= $request_limit) {
// Block the IP address
echo “IP address $client_ip has been blocked due to excessive requests.”;
// Optionally, you can log this event or take further actions (e.g., send an email to the administrator).
} else {
// Process the request
echo “Request from IP address $client_ip is allowed.”;
// Update the request count for the IP address
$ip_counts[$client_ip] = isset($ip_counts[$client_ip]) ? $ip_counts[$client_ip] + 1 : 1;
// Save the updated IP counts to the file
file_put_contents($filename, json_encode($ip_counts));
}
This script checks the number of requests from a specific IP address and blocks it if the limit is exceeded. The request counts are stored in a JSON file (ip_counts.txt in this example). This is a simple example, and in a real-world scenario, you might want to use a more robust storage solution or database for scalability and reliability.
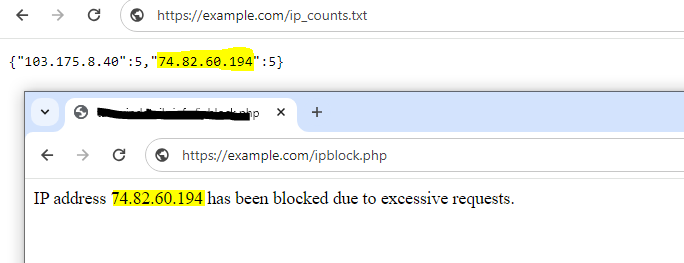
Keep in mind that IP-based rate limiting has limitations, and for more advanced scenarios, you might want to consider using a dedicated rate-limiting mechanism or a web application firewall. Additionally, blocking IP addresses should be done cautiously, and it’s essential to consider potential false positives and the impact on legitimate users.
Second Methods